Fascination About Risk Management Enterprise
Table of ContentsExcitement About Risk Management EnterpriseRumored Buzz on Risk Management EnterpriseGetting My Risk Management Enterprise To Work
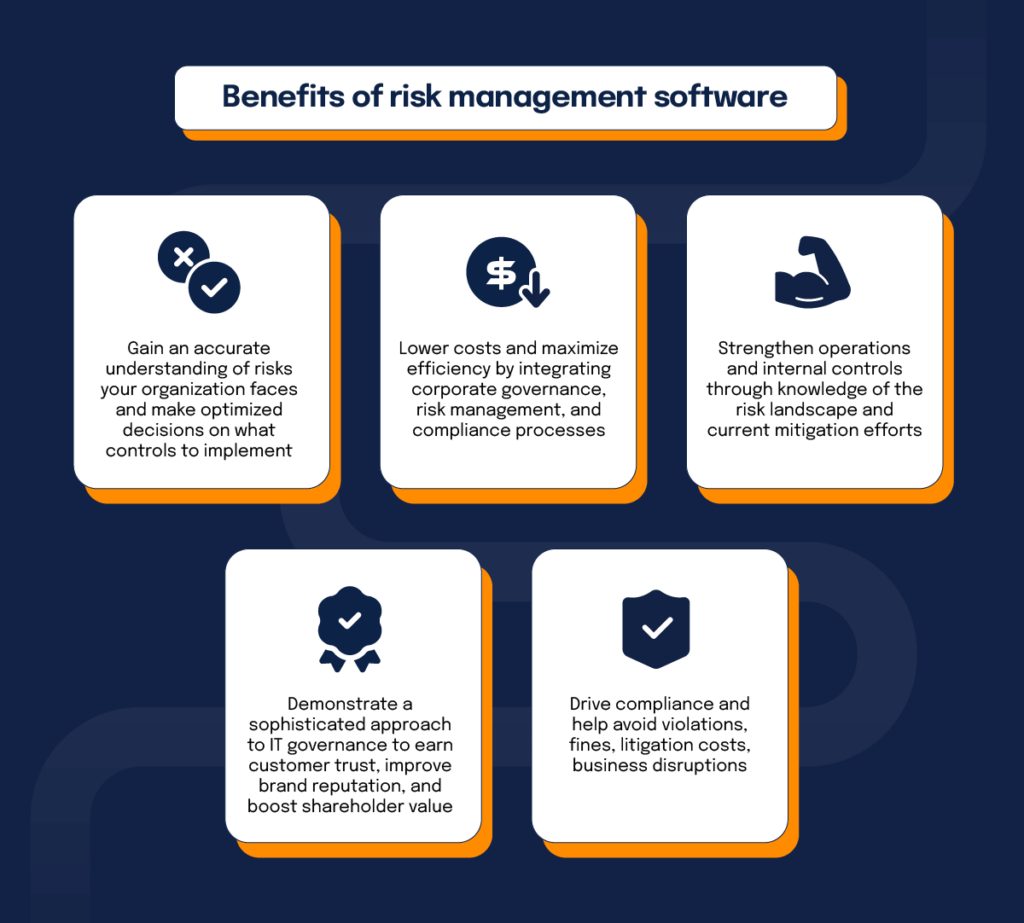
Control who can see or modify these aspects by setting specific access rights for individual users, making sure details protection and customized usability. Allows users to customize their user interface by picking and arranging essential data elements. Gives a personalized experience by allowing personalization of where and just how data aspects are displayed.It enables access to real-time incorporated data quickly. Risk Management Enterprise. This assists remove wasted time on hands-on record compilation. Additionally, centers can use detailed information intelligence for quicker and a lot more educated decision-making. Additionally, it permits the automated development of stakeholder records for individuals or teams. Allows timely decision-making and lowers hold-ups triggered by obsolete details.
Diligent is a risk administration software program that permits optimizing performance, and enhances development. It likewise aids keep an eye on threats with ERM software that includes incorporated analytics and adapts to your service needs.
The Greatest Guide To Risk Management Enterprise
Streamlines the process of collecting risk information from different parts of the organization. Offers management and the board with real-time threat insights. Usage ACL's sophisticated analytics to detect threat patterns and anticipate hazards.
This enables business to capture risk insights and red flags in the third-party supplier's safety and security report. Allows firms to record and document threat insights and red flags in third-party supplier protection reports.
It additionally lowers danger via structured conformity and threat monitoring. It can assist gather and track all your threats in the Hyperproof threat register.
It makes sure that everything is arranged and easily accessible for auditors. Uses automation to keep proof updated while minimizing hands-on effort. It gives quick access to required information and documents. This guarantees the protection of Active proof circumstances by making it possible for multi-factor verification (MFA) using authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
Not known Facts About Risk Management Enterprise
It provides top-tier protection functions to protect delicate data. This threat administration software application is a best tool for centers looking to fix unnecessary problems or dangers.
Customers can also use the AI-powered tools and pre-existing material to produce, evaluate, focus on, and address threats effectively. Enhances the procedure of setting up and inhabiting threat signs up. Makes use of AI and collection web content to boost risk assessment precision. It allows much faster identification and mitigation of risks, This is primarily a visual model.